This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!-----------------------------------------!
! VRF-Aware Policy-Based IKEv1 VPN !
!-----------------------------------------!
!
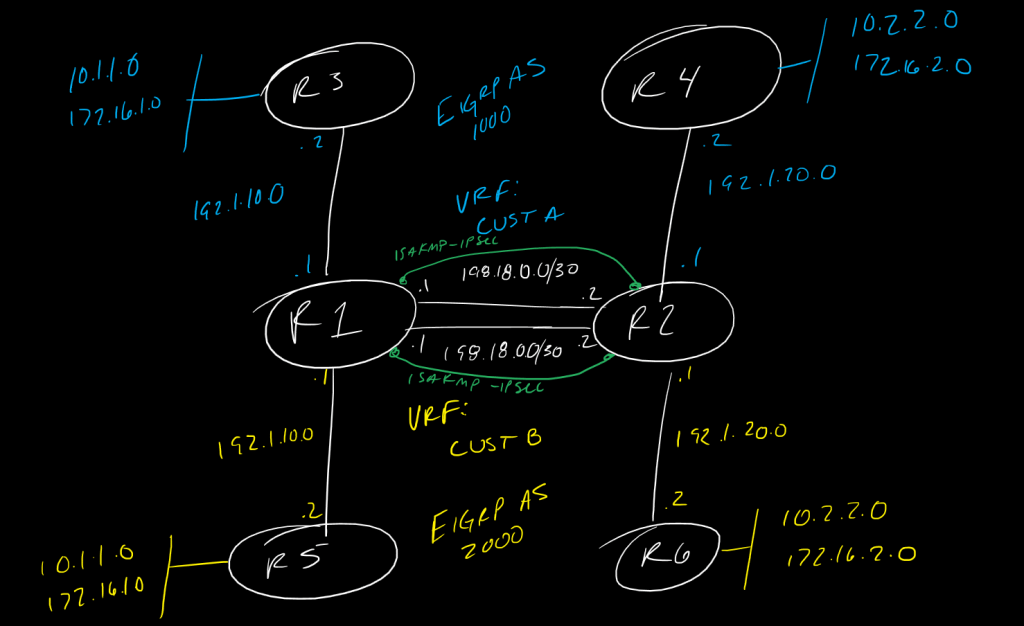
!In this topology we have two VRFs, custa and custb, with duplicate IP space and a policy-based tunnel spun up dynamically to encrypt traffic across R1 and R2, our "SP" routers. The goal is to provide direct reachability across customer routers but encrypt the traffic flowing within the SP cloud.
!
!
!-------
! R1
!-------
!
!first we define the VRFs needed
!
vrf definition custa
!
address-family ipv4
exit-address-family
!
vrf definition custb
!
address-family ipv4
exit-address-family
!
!
!Next we can configure the interfaces in the proper VRFs
!
interface Ethernet0/0
vrf forwarding custa
ip address 198.18.0.1 255.255.255.252
!
interface Ethernet0/1
vrf forwarding custb
ip address 198.18.0.1 255.255.255.252
!
interface Ethernet0/2
vrf forwarding custa
ip address 192.1.10.1 255.255.255.0
!
interface Ethernet0/3
vrf forwarding custb
ip address 192.1.10.1 255.255.255.0
!
!
!then we can create a VRF-aware dynamic routing configuration with EIGRP to allow underlay forwarding
!
router eigrp 100
!
address-family ipv4 vrf custa autonomous-system 1000
network 192.1.10.0
network 198.18.0.0 0.0.0.3
exit-address-family
!
address-family ipv4 vrf custb autonomous-system 2000
network 192.1.10.0
network 198.18.0.0 0.0.0.3
exit-address-family
!
!
!now we can configure a basic ISAKMP policy
!
crypto isakmp policy 5
encr aes
authentication pre-share
group 19
lifetime 28800
!
!since we have to tie the PSK to a vrf, we need keyrings
!
!crypto keyring KR-custa vrf custa
pre-shared-key address 0.0.0.0 0.0.0.0 key C@sco123!
crypto keyring KR-custb vrf custb
pre-shared-key address 0.0.0.0 0.0.0.0 key C@sco123!
!
!now that we have our keyrings, we need to create ISAKMP profiles to allow the keyrings to bind to the correct VRF; we need to define the vrf, keyring, and match identity
!
crypto isakmp profile custa-isakmp-profile
vrf custa
keyring KR-custa
match identity address 0.0.0.0 custa
crypto isakmp profile custb-isakmp-profile
vrf custb
keyring KR-custb
match identity address 0.0.0.0 custb
!
!now we can configure our transform-set normally
!
crypto ipsec transform-set TFS esp-aes esp-sha-hmac
mode tunnel
!
!
!here we will create our interesting traffic ACLs - technically because the IP space is identical it could be a single ACL but for testing, we will make 100 for custa and 101 for custb
!
!
access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
!
!
!now we can create our cryptomaps - we will need one per vrf
!
crypto map custa-cryptoMap isakmp-profile custa-isakmp-profile
crypto map custa-cryptoMap 10 ipsec-isakmp
set peer 198.18.0.2
set transform-set TFS
match address 100
!
crypto map custb-cryptoMap isakmp-profile custb-isakmp-profile
crypto map custb-cryptoMap 10 ipsec-isakmp
set peer 198.18.0.2
set transform-set TFS
match address 101
!
!
!finally we can tie the cryptomap to the relevant interfaces
!
interface Ethernet0/0
crypto map custa-cryptoMap
!
interface Ethernet0/1
crypto map custb-cryptoMap
!
!
!
!--------
! R2
!--------
!
!now we can rinse and repeat for R2, adjusting IPs as needed
!
vrf definition custa
!
address-family ipv4
exit-address-family
!
vrf definition custb
!
address-family ipv4
exit-address-family
!
!
interface Ethernet0/0
vrf forwarding custa
ip address 198.18.0.2 255.255.255.252
!
interface Ethernet0/1
vrf forwarding custb
ip address 198.18.0.2 255.255.255.252
!
interface Ethernet0/2
vrf forwarding custa
ip address 192.1.20.1 255.255.255.0
!
interface Ethernet0/3
vrf forwarding custb
ip address 192.1.20.1 255.255.255.0
!
!
router eigrp 100
!
address-family ipv4 vrf custa autonomous-system 1000
network 192.1.20.0
network 198.18.0.0 0.0.0.3
exit-address-family
!
address-family ipv4 vrf custb autonomous-system 2000
network 192.1.20.0
network 198.18.0.0 0.0.0.3
exit-address-family
!
!
crypto isakmp policy 5
encr aes
authentication pre-share
group 19
lifetime 28800
!
!crypto keyring KR-custa vrf custa
pre-shared-key address 0.0.0.0 0.0.0.0 key C@sco123!
crypto keyring KR-custb vrf custb
pre-shared-key address 0.0.0.0 0.0.0.0 key C@sco123!
!
crypto isakmp profile custa-isakmp-profile
vrf custa
keyring KR-custa
match identity address 0.0.0.0 custa
crypto isakmp profile custb-isakmp-profile
vrf custb
keyring KR-custb
match identity address 0.0.0.0 custb
!
!now we can configure our transform-set normally
!
crypto ipsec transform-set TFS esp-aes esp-sha-hmac
mode tunnel
!
!
access-list 100 permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
access-list 101 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
!
crypto map custa-cryptoMap isakmp-profile custa-isakmp-profile
crypto map custa-cryptoMap 10 ipsec-isakmp
set peer 198.18.0.1
set transform-set TFS
match address 100
!
crypto map custb-cryptoMap isakmp-profile custb-isakmp-profile
crypto map custb-cryptoMap 10 ipsec-isakmp
set peer 198.18.0.1
set transform-set TFS
match address 101
!
!
interface Ethernet0/0
crypto map custa-cryptoMap
!
interface Ethernet0/1
crypto map custb-cryptoMap
!
!--------------------------------
! Verifications
!--------------------------------
!
sh vrf
show ip route vrf <vrf>
traceroute vrf
ping vrf
show ip protocols
sh cry isakmp-profile
sh crypto map
show crypto isakmp sa [detail]
show crypto ipsec sa [detail]
!
!