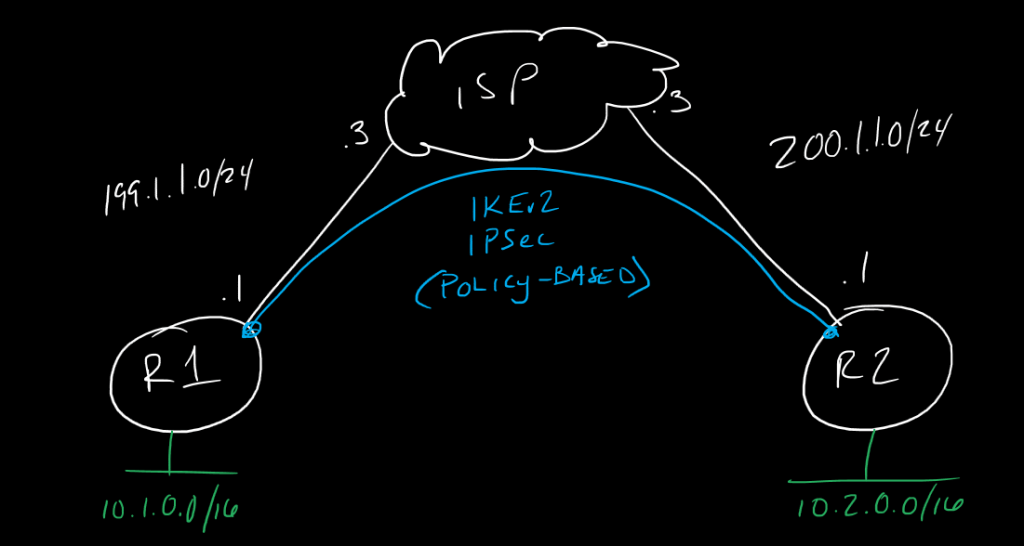
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!-------------------------------------------!
! Basic IKEv2 Policy-based VPN on IOS !
!-------------------------------------------!
!
!with IKEv2 we gain some scalability benefits along with other security features like PRF and anti-replay
!aside from the Phase 1 config being different and arguably more complex, the configuration workflow is basically the same as IKEv1/ISAKMP
!
!--------
! R1
!--------
!
!first we can create a couple of Lo addresses to ping along with our underlay interface eth0/0
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface Loopback1
ip address 10.1.2.1 255.255.255.0
!
interface Ethernet0/0
ip address 199.1.1.1 255.255.255.0
!
!lets add a route for underlay routing
!
ip route 0.0.0.0 0.0.0.0 199.1.1.3
!
!now, we start with Phase1 and the IKEv2 proposal, which basically replaces the ISAKMP policy config used in IKEv1. the proposal lets us configure lists of attributes which are acceptable as opposed to having to define static policy conditions like we do in ISAKMP, so it is considerably more scalable and easier to manage
!
crypto ikev2 proposal PBVPN
encryption aes-cbc-128 aes-cbc-192 aes-cbc-256
integrity sha256 sha384 sha512
group 19 20 21 14
!
!we will then define a quick policy to activate the proposal - note that IKEv2 on IOS has "smart-defaults" which include a lot of "default" configs out of the box
!show run all | incl crypto is one way to see them, or show crypto <feature> default
!we could pin this to specific local addresses of VRFs here too
!
crypto ikev2 policy PBVPN-policy
proposal PBVPN
!
!now we will create a keyring, which is the only way IKEv2 does PSK no individual commands. IKEv2 allows for remote and local auth methods to be different and also allwos for keys to be different if both sides are using pre-shared keys, so, lets define our peer (R2) and they keys we want to use for phase 1 traffic-key exchange encryption
!
crypto ikev2 keyring PBVPN-KR
peer R2
address 200.1.1.1
pre-shared-key local P@ssw0rd!
pre-shared-key remote C1sco123!
!
!
!now we can define the ikev2 profile, which ties the peer identity to the auth methods and maps the keyring
!
crypto ikev2 profile PBVPN-prof
match identity remote address 200.1.1.1 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local PBVPN-KR
!
!
!now, we can configure phase 2 normally, starting with an interesting traffic ACL and IPSec transform-set
!
access-list 100 permit ip 10.1.0.0 0.0.255.255 10.2.0.0 0.0.255.255
!
crypto ipsec transform-set TFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
!
!we can now finally configure the crypto map and apply to the interface
!note the set ikev2-profile command, this is what forces the cryptomap to use IKEv2, if this is missing it will use ISAKMP/IKEv1
!
crypto map ikev2-pbvpn 10 ipsec-isakmp
set peer 200.1.1.1
set transform-set TFS
set ikev2-profile PBVPN-prof
match address 100
!
interface Ethernet0/0
crypto map ikev2-pbvpn
!
!
!---------
! R2
!---------
!
!configure R2 the same with IP elements adjusted as needed
!
interface Loopback0
ip address 10.2.1.1 255.255.255.0
!
interface Loopback1
ip address 10.2.2.1 255.255.255.0
!
interface Ethernet0/0
ip address 200.1.1.1 255.255.255.0
!
!lets add a route for underlay routing
!
ip route 0.0.0.0 0.0.0.0 200.1.1.3
!
crypto ikev2 proposal PBVPN
encryption aes-cbc-128 aes-cbc-192 aes-cbc-256
integrity sha256 sha384 sha512
group 19 20 21 14
!
crypto ikev2 policy PBVPN-policy
proposal PBVPN
!
crypto ikev2 keyring PBVPN-KR
peer R1
address 199.1.1.1
pre-shared-key local C1sco123!
pre-shared-key remote P@ssw0rd!
!
!note that the keys get reversed here because OUR local key on R2 was defined as the REMOTE key on R1 and vice-versa
!
!
crypto ikev2 profile PBVPN-prof
match identity remote address 199.1.1.1 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local PBVPN-KR
!
!
!now, we can configure phase 2 normally, starting with an interesting traffic ACL and IPSec transform-set
!
access-list 100 permit 10.2.0.0 0.0.255.255 ip 10.1.0.0 0.0.255.255
!
crypto ipsec transform-set TFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto map ikev2-pbvpn 10 ipsec-isakmp
set peer 199.1.1.1
set transform-set TFS
set ikev2-profile PBVPN-prof
match address 100
!
interface Ethernet0/0
crypto map ikev2-pbvpn
!
!
!-------------------------
! Verifications
!-------------------------
!
show cry ikev1 proposal
show crypto ikev2 policy
show crypto ikev2 profile
show crypto map
show crypto ikev2 sa [detail]
show crypto ipsec sa [detail]
