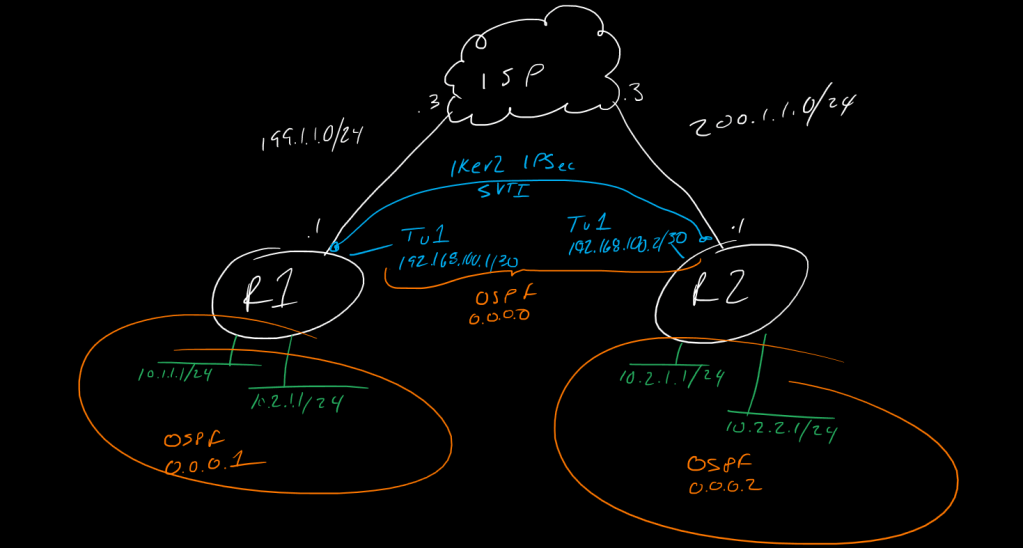
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!--------------------------------------------!
! IKEv2 Route-Based VPN using sVTI on IOS !
!--------------------------------------------!
!
!We configure this the same was as policy-based VPN, except instead of a crypto map we apply an IPSec profile, just like in the IKEv1 workflow.
!
!--------
! R1
!--------
!
!first we can create a couple of Lo addresses to ping along with our underlay interface eth0/0
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface Loopback1
ip address 10.1.2.1 255.255.255.0
!
interface Ethernet0/0
ip address 199.1.1.1 255.255.255.0
!
!lets add a route for underlay routing
!
ip route 0.0.0.0 0.0.0.0 199.1.1.3
!
!Now we can configure IKEv2 phase 1 and 2 just like the policy-based example, up until we would create the Crypto Map, as we don't need that here:
!
!1. Proposal
!2. Policy
!3. Keyring
!4. Profile
!
cry ikev2 proposal myProp
integrity sha256 sha384
group 2 5 19 24
encry aes-cbc-128 aes-cbc-256
!
cry ikev2 policy default
proposal myProp
!
cry ikev2 keyring ikev2-KR
peer Router2
address 200.1.1.1
pre-shared-key S3cur1ty123
!If we only define one key like this, it is used for both local and remote
!
cry ikev2 profile ikev2-Prof
match identity remote address 200.1.1.1 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local ikev2-KR
!
cry ipsec transform-set TFS esp-aes esp-sha-hmac
mode transport
!
!now instead of an ACL and Cryptomap, we configure an IPSec profile
!
!
crypto ipsec profile ikev2-ipsec-prof
set transform-set TFS
set ikev2-profile ikev2-Prof
!
!
!finally, we can create a tunnel interface, address it, and apply the profile, followed by standing up a basic IGRP config with OSPF
!
!
int tu1
ip add 192.168.100.1 255.255.255.252
tunnel source eth0/0
tunnel destination 200.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ikev2-ipsec-prof
!
router ospf 1
network 10.1.1.0 0.0.0.255 area 0.0.0.1
network 10.1.2.0 0.0.0.255 area 0.0.0.1
network 192.168.100.0 0.0.0.255 area 0.0.0.0
!
!
!and of course, add the same config with adjustments as needed on the peer router
!
!--------
! R2
!--------
!
interface Loopback0
ip address 10.2.1.1 255.255.255.0
!
interface Loopback1
ip address 10.2.2.1 255.255.255.0
!
interface Ethernet0/0
ip address 200.1.1.1 255.255.255.0
!
!lets add a route for underlay routing
!
ip route 0.0.0.0 0.0.0.0 200.1.1.3
!
cry ikev2 proposal myProp
integrity sha256 sha384
group 2 5 19 24
encry aes-cbc-128 aes-cbc-256
!
cry ikev2 policy default
proposal myProp
!
cry ikev2 keyring ikev2-KR
peer Router2
address 199.1.1.1
pre-shared-key S3cur1ty123
!
cry ikev2 profile ikev2-Prof
match identity remote address 199.1.1.1 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local ikev2-KR
!
cry ipsec transform-set TFS esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile ikev2-ipsec-prof
set transform-set TFS
set ikev2-profile ikev2-Prof
!
int tu1
ip add 192.168.100.2 255.255.255.252
tunnel source eth0/0
tunnel destination 199.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ikev2-ipsec-prof
!
router ospf 1
network 10.2.1.0 0.0.0.255 area 0.0.0.2
network 10.2.2.0 0.0.0.255 area 0.0.0.2
network 192.168.100.0 0.0.0.255 area 0.0.0.0
!
int tu1
ip ospf authentication message-digest
ip ospf authentication-key OSPF-4U
!
!
!--------------------------!
! Verifications !
!--------------------------!
!
show crypto ikev1 proposal
show crypto ikev2 policy
show crypto ikev2 profile
show crypto ikev2 sa [detail]
show crypto ipsec sa [detail
debug crypto ikev2
debug crypto ipsec
show ip protocols
show ip ospf neighbor detail
show int tu1