This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!------------------------------------------------!
! FlexVPN with Negotiated Tunnels and PSK Auth !
!------------------------------------------------!
!
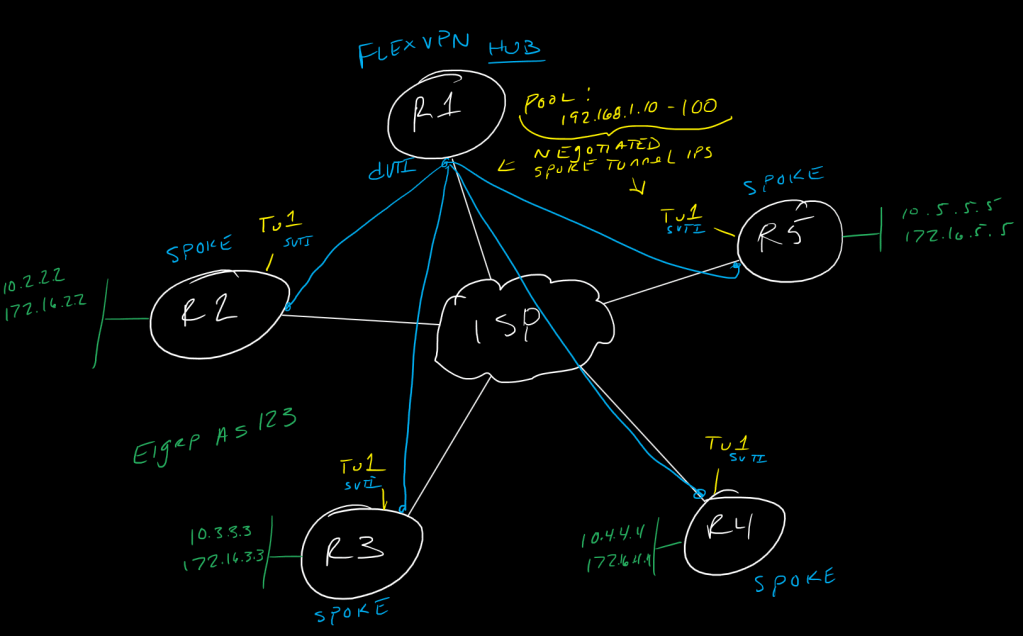
!building on sVTI/dVTI, FlexVPN allows for hub and spoke or dynamic spoke-to-spoke WAN mesh/partial mesh while also supporting the ability to configure AnyConnect on IOSs routers since it is IKEv2 based, and as IKEv2 is able to support EAP it provides a huge number of options for authentication/authorization. thgouh flexVPN is more complex config and requires some additional planning vs DMVPN, it does, admittedly, give us some nice scalability options. You can use the Hub to manage spoke tunnel IP assignment, so in a large deployment you can have a single configuration to drop on any spoke router for example with no changes needed.
!
!-----------
! Spokes
!-----------
!
!we'll start with our spoke routers and configure a hub-and-spoke topology, without the use of nhrp shortcut and virtual-access interfaces on the spoke side, only on the hub/hubs. So, from the spoke perspective, really this is just an IKEv2 sVTI configuration. We will configure our spokes to negotiate the IP of their tunnel interface from a pool on the hub, which is done on the hub-side configuration using the ikev2 authorization policy.
!
!
!start with the basics of IKEv2:
!
!1. Proposal
!2. Policy
!3. Keyring
!4. Profile
!
crypto ikev2 proposal flexProp
integrity sha256 sha384
group 19
encry 3des aes-cbc-128
!
crypto ikev2 policy flexPolicy
match fvrf any
proposal flexProp
!
crypto ikev2 keyring flexKR
peer Hub-Router
address 0.0.0.0
pre-shared-key local iamasp0ke!
pre-shared-key remote iamth3hub!
!
crypto ikev2 profile flexProfile
authentication local pre-share
authentication remote pre-share
match identity remote address 0.0.0.0
keyring local flexKR
!
!
!configure phase 2 as normal
!
crypto ipsec transform-set flexTFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile flexIPSecProfile
set transform-set flexTFS
set pfs group19
set ikev2-profile flexProfile
!
!configure the sVTI tunnel interface using the ip address negotiated command to allow the spoke to request an IP from the hub pool once IKEv2 authentication has completed
!
int tu1
ip address negotiated
tunnel source eth0/0
tunnel destination 192.1.10.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile flexIPSecProfile
!
!configure some basic routing, we have a couple of loopbacks in the 10 and 172 space already configured
!
router eigrp 123
network 10.0.0.0
network 172.16.0.0
network 192.168.1.0 0.0.0.255
!
!
!------------
! Hub
!------------
!
!now, on the hub, we create a basic dVTI configuration, but with a couple of additional things:
!
!1. enable aaa new-model and configure aaa authorization network method list
!2. create an ip local pool for spoke tunnel IP assignment
!3. edit the default ikev2 authorization policy to reference the pool and ensure route set interface is configured
!
!
aaa new-model
aaa authorization network default local
!
!
ip local pool SpokeTunnels 192.168.1.10 192.168.1.100
!
crypto ikev2 authorization policy default
pool SpokeTunnels
route set interface
!
crypto ikev2 proposal flexProp
integrity sha256 sha384
group 19
encry 3des aes-cbc-128
!
crypto ikev2 policy flexPolicy
match fvrf any
proposal flexProp
!
crypto ikev2 keyring flexKR
peer Spoke-Routers
address 0.0.0.0
pre-shared-key remote iamasp0ke!
pre-shared-key local iamth3hub!
!
crypto ikev2 profile flexProfile
authentication local pre-share
authentication remote pre-share
match identity remote address 0.0.0.0
keyring local flexKR
aaa authorization group override psk list default default
!! this line says for PSK based IKEv2-auth, use the default method list and the default ikev2 authorization policy
!
crypto ipsec transform-set flexTFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile flexIPSecProfile
set transform-set flexTFS
set pfs group19
set ikev2-profile flexProfile
!
interface Lo192
ip add 192.168.1.1 255.255.255.0
!
interface virtual-template 1 type tunnel
ip unnumbered lo192
tunnel source eth0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile flexIPSecProfile
!
crypto ikev2 profile flexProfile
virtual-template 1
!
router eigrp 123
network 10.0.0.0
network 172.16.0.0
network 192.168.1.0 0.0.0.255
!
!
!-------------------------!
! Verifications !
!-------------------------!
!
!
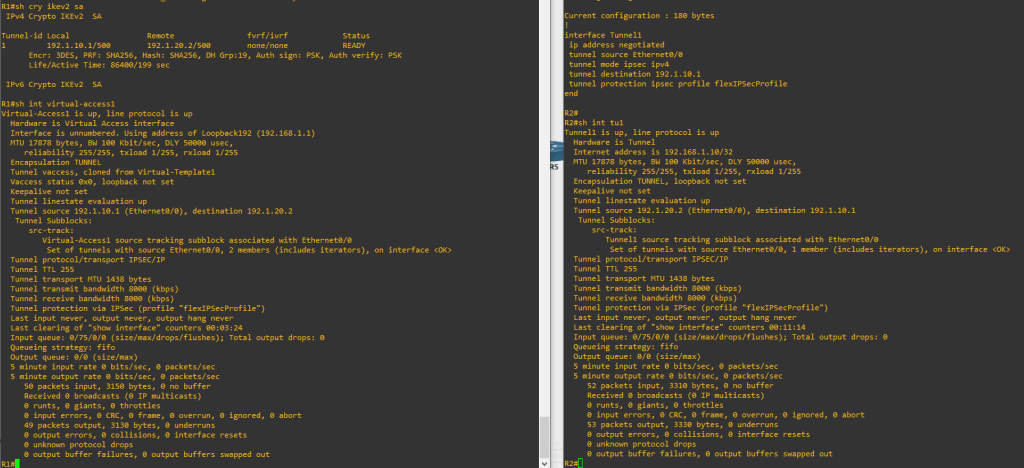
show crypto ikev2 sa
show crypto ipsec sa
show crypto ikev2 proposal
show crypto ikev2 policy
show crypto ikev2 keyring
show crypto ikev2 profile
show crypto ipsec profile
show run aaa
show run all | sec crypto
show ip local pool <poolName>
show int virtual-access[n]
debug crypto ikev2
debug crypto ipsec