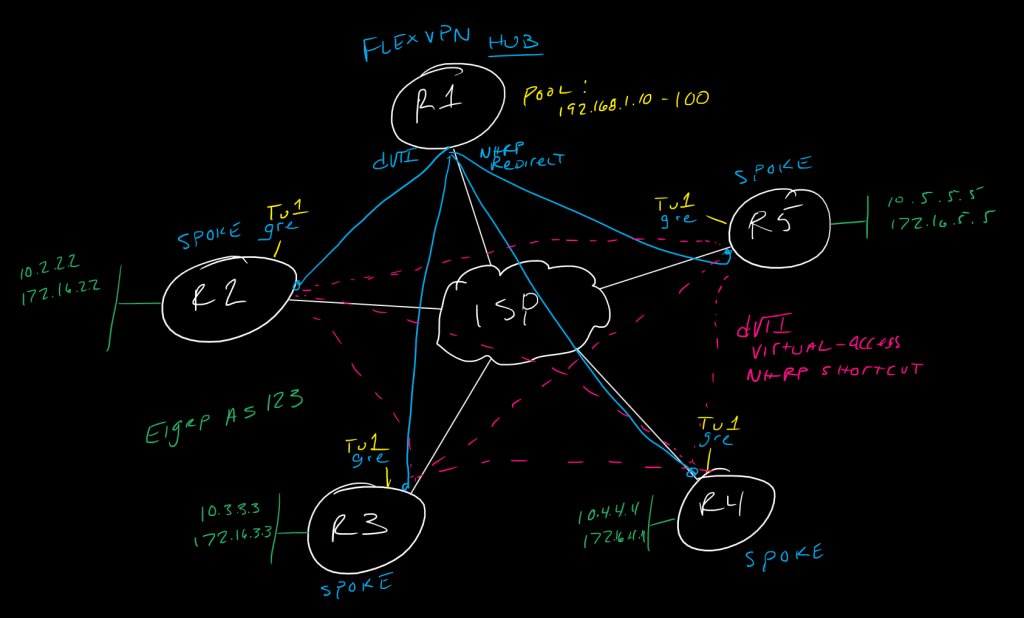
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!----------------------------------------!
! FlexVPN PSK Spoke-to-Spoke (PSK Auth) !
!----------------------------------------!
!
!To configure FlexVPN and allow dynamic Spoke to Spoke tunnels, we need to do a few things differently from the Hub and Spoke config:
!
!1. configure all of our tunnels as mode gre ip, not ipsec ipv4, since we need to encapsulate nhrp
!2. configure ip nhrp redirect on the hub
!3. configure a virtual-template interface on the spokes
!4. configure ip nhrp shortcut on the spokes
!5. configure the same aaa and ikev2 authorization commands from the hub on the spokes
!6. use the same local/remote psk, since now spokes need to auth to the hub as well as to each other
!
!in an ideal world, we would also consider routing optimizations, since the spoke-to-spoke tunnels are direct dVTI, not multipoint GRE with multicast mapping like DMVPN - as such, spokes will actually form EIGRP peer relationships with each other, so in a real deployment that overhead needs to be able to be accounted for with hardware and software limitations etc.
!
!
!------------
! Hub
!------------
!
!configure our aaa and authz for ikev2 peer auth
!
aaa new-model
aaa authorization network default local
!
!
ip local pool SpokeTunnels 192.168.1.10 192.168.1.100
!
!start with the basics of IKEv2:
!
!1. Proposal
!2. Policy
!3. Keyring
!4. Profile
!
crypto ikev2 authorization policy default
pool SpokeTunnels
route set interface
!
crypto ikev2 proposal flexProp
integrity sha256 sha384
group 19
encry 3des aes-cbc-128
!
crypto ikev2 policy flexPolicy
match fvrf any
proposal flexProp
!
crypto ikev2 keyring flexKR
peer FlexVPN-Peers
address 0.0.0.0
pre-shared-key Fl3xVPN!!
!
crypto ikev2 profile flexProfile
authentication local pre-share
authentication remote pre-share
match identity remote address 0.0.0.0
keyring local flexKR
aaa authorization group override psk list default default
virtual-template 1
!
!configure phase 2
!
crypto ipsec transform-set flexTFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile flexIPSecProfile
set transform-set flexTFS
set pfs group19
set ikev2-profile flexProfile
!
interface Lo192
ip add 192.168.1.1 255.255.255.0
!
interface virtual-template 1 type tunnel
ip unnumbered lo192
tunnel source eth0/0
ip nhrp network-id 1
ip nhrp redirect
tunnel protection ipsec profile flexIPSecProfile
!
!and add some EIGRP
!
router eigrp 123
network 10.0.0.0
network 172.16.0.0
network 192.168.1.0 0.0.0.255
!
!-----------
! Spokes
!-----------
!
!
aaa new-model
aaa authorization network default local
!
crypto ikev2 authorization policy default
route set interface
!
!start with the basics of IKEv2 just like the hub, note the single psk
!
!1. Proposal
!2. Policy
!3. Keyring
!4. Profile
!
crypto ikev2 proposal flexProp
integrity sha256 sha384
group 19
encry 3des aes-cbc-128
!
crypto ikev2 policy flexPolicy
match fvrf any
proposal flexProp
!
crypto ikev2 keyring flexKR
peer FlexVPN-Peers
address 0.0.0.0
pre-shared-key Fl3xVPN!!
!
crypto ikev2 profile flexProfile
authentication local pre-share
authentication remote pre-share
match identity remote address 0.0.0.0
keyring local flexKR
aaa authorization group override psk list default default
virtual-template 1
!
!
!configure phase 2
!
crypto ipsec transform-set flexTFS esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile flexIPSecProfile
set transform-set flexTFS
set pfs group19
set ikev2-profile flexProfile
!
!configure our virtual-template interface which we will reference in the nhrp shortcut command to say "hey, when we get an NHRP resolution for this remote network, spin up a virtual-access dVTI tunnel to that peer." We will also base the virtual-template IP on the dynamically negotiated IP used for the sVTI interface pointing to the hub - this is not a requirement, we can make this IP whatever we want, but in the interest of a simplified template this is pretty common
!
int virtual-template 1 type tunnel
ip unnumbered tu1
tunnel source eth0/0
ip nhrp network-id 1
ip nhrp shortcut
tunnel protection ipsec profile flexIPSecProfile
!
int tu1
ip address negotiated
tunnel source eth0/0
tunnel destination 192.1.10.1
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
tunnel protection ipsec profile flexIPSecProfile
!
!configure some basic routing, we have a couple of loopbacks in the 10 and 172 space already configured
!
router eigrp 123
network 10.0.0.0
network 172.16.0.0
network 192.168.1.0 0.0.0.255
!
!
!-------------------------!
! Verifications !
!-------------------------!
!
!
show crypto ikev2 sa
show crypto ipsec sa
show crypto ikev2 proposal
show crypto ikev2 policy
show crypto ikev2 keyring
show crypto ikev2 profile
show crypto ipsec profile
show derived-config int virtual-access1
show run aaa
show run all | sec crypto
show ip local pool <poolName>
show int virtual-access[n]
debug crypto ikev2
debug crypto ipsec