This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
Transparent ASA Notes
- Bump in the wire deployment, no need to change layer 3 topology to insert security control
- BPDUs and ARP are allowed by default
- IP traffic is enabled for inspection by default and cannot be denied, even with an ethertype ACL
- MAC addresses of traffic entering the ASA is learned per usual and added to the MAC table with a default 300s timeout
Check the mode: show firewall
Mode Router == standard L3 firewall
Mode Transparent == transparent L2 firewall
At config prompt: firewall transparent
This will nuke all existing configuration but only in the running config, startup config will not be touched yet, so a reboot could save it
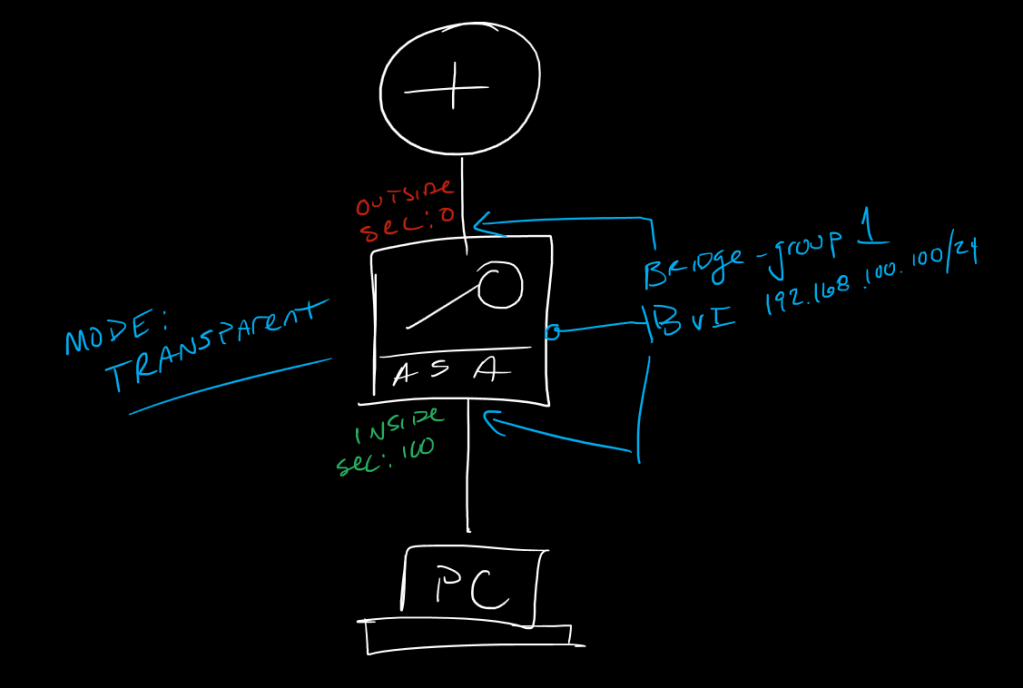
L2 domain is called Bridge Domain
To bridge segments together use bridge-group command on interface
Interfaces still need nameif and security level
int gig0/0
nameif outside
security-level 0
bridge-group 1
!
int gig0/1
nameif inside
Security-level 100
bridge-group 1
!Connected networks within the same bridge group must be on the same subnet
BVI can be created (bridge virtual interface), sort of like an SVI, not required unless IP features are needed on the firewall like NAT, commonly used for out-of-band management though
BVI should NOT be used as a gateway IP for downstream clients needing to pass through the firewall, they should use a L3 interface on an upstream device in the same bridge group
You can use mgmt0/0 for mgmt or you can use BVI for inband
interface bvi1
ip add 192.168.100.100 255.255.255.0
!!!! Implicit high -> low traffic initiation based on security level is only allowed for unicast traffic !!!
So to allow multicast or broadcast traffic such as broadcast ARPs, dynamic routing hello messages, etc., you have to ACL it as well, useful to know if you have something trying to form eigrp etc whatever.
Unsupported features in Transparent mode:
- Dynamic DNS
- DHCP Relay (DHCPd server is supported still)
- Participation in dynamic routing protocols (can pass this through but BVI cannot peer)
- QoS
- VPN Termination for data plane – it can terminate VPN but ONLY for management plane traffic TO the box, not through – VPN traffic can be passed through the box using ACL as you would expect
- UC features
Good general document – https://www.cisco.com/c/en/us/td/docs/security/asa/asa91/asdm71/general/asdm_71_general_config/intro_fw.pdf
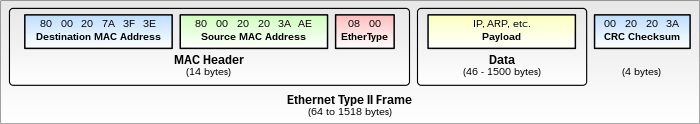
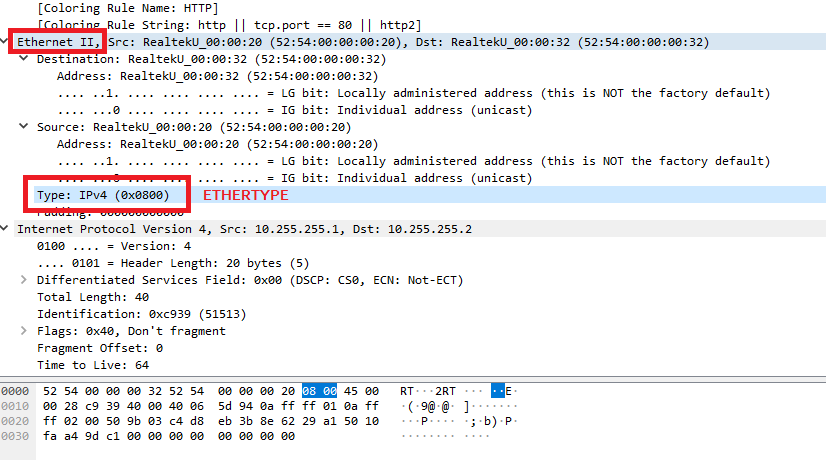
ETHERTYPE ACL
Used to allow traffic based on ethertype field value in ethernet header. Ethertype is basically the identifier for the network layer protocol in use. 2 byte hex value 0x0600-0xffff. Also counts for 802.3 ethernet I frames used by spanning tree, which use length bytes instead of type bytes.
https://en.wikipedia.org/wiki/EtherType
IP (0x0800) is allowed by default
Other non-IP protocols like bpdu, mpls, etc. are listed by default in ASA
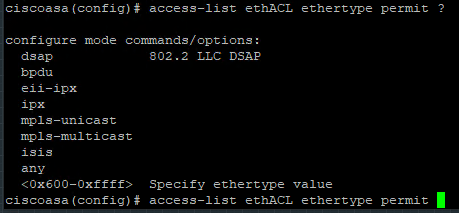
access-list ethACL ethertype permit <ethertype_value>
access-group ethACL in interface <interface>One ACL, per type, per direction, can be applied to each inerface. L3 ACL, L2 ethertype ACL, control-plane ACL.