This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies.
!---------------------------!
! IKEv1 tunnel Through !
! an ASA with NAT-T !
!---------------------------!
!
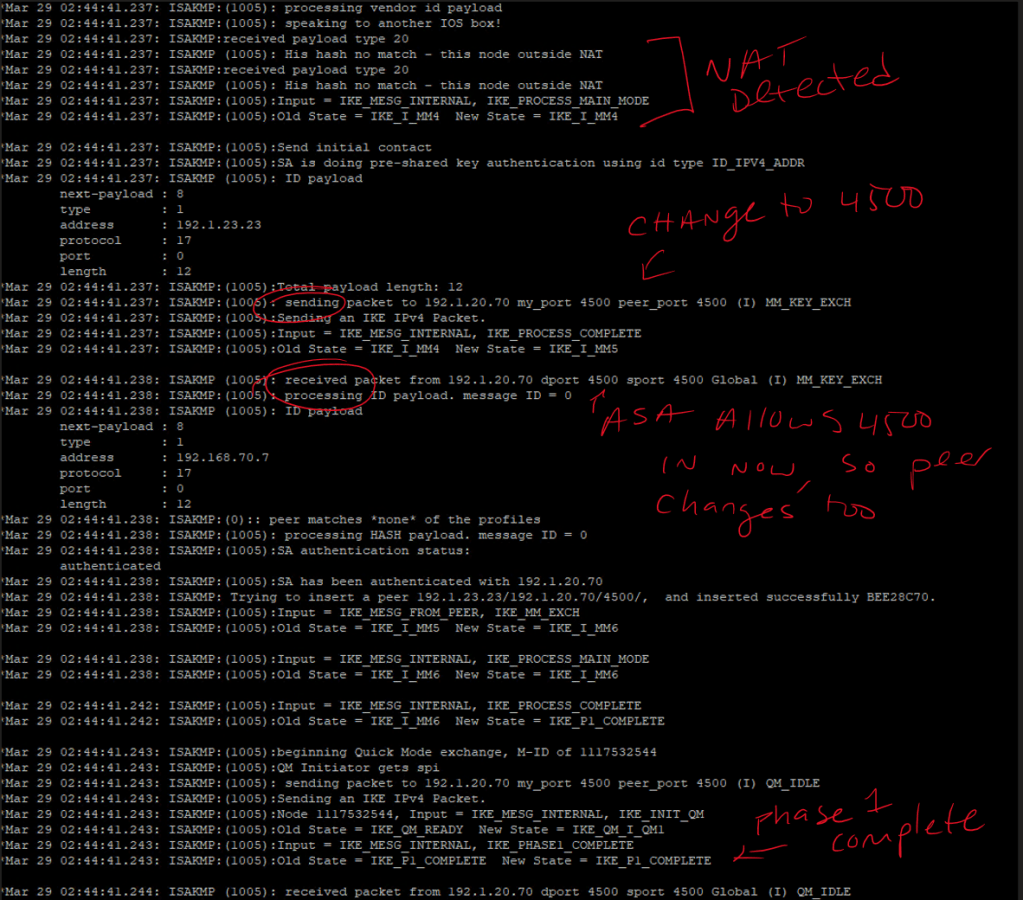
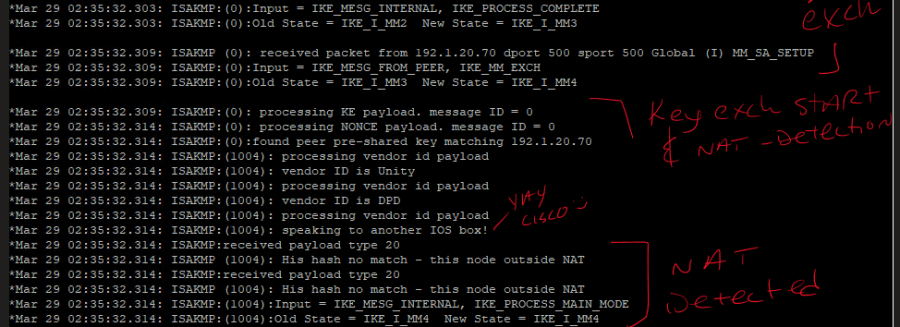
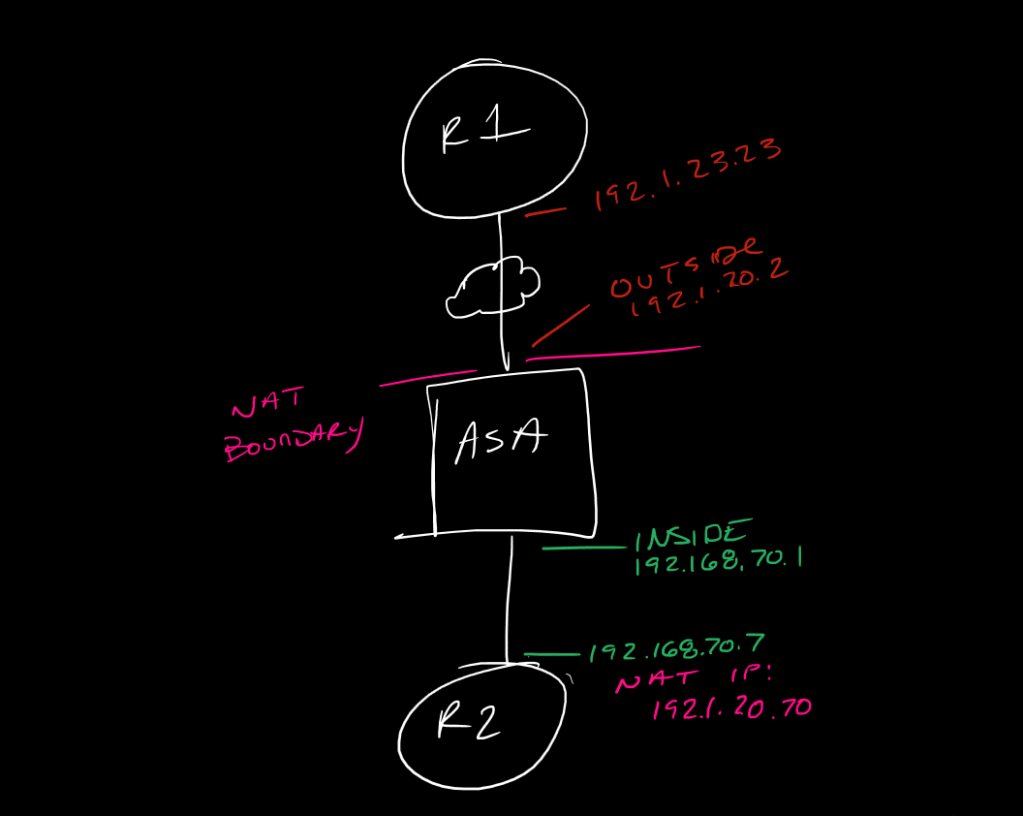
!here we will configure a basic GREoIPSec tunnel between two routers through an ASA, but one of the routers is assigned a privtate IP on the outside interface and is being NATted to a public IP on the outside of the ASA, which will trigger NAT-Traversal detection during ISAKMP Phase 1 exchange and cause the peers to switch from UDP500 for ISAKMP over to UDP4500 - note that the UDP4500 header will encapsulate *the entire packet*, so, the ASA will not actually even see ESP at all, just the brief exchange at UDP:500 and then persistent traffic at UDP:4500 for NAT-T.
!
!-------
! R1
!-------
!
!create basic VTI tunnel with IPSec, pointing to the NAT IP of the R2 router
!
crypto isakmp policy 10
authentication pre-share
hash sha256
group 19
lifetime 3600
encryption aes 256
!
crypto isakmp key cisco123! address 192.1.20.70
!
crypto ipsec transform-set TFS esp-aes 256 esp-sha256-hmac
mode transport
!
crypto ipsec profile IPSEC
set transform-set TFS
!
int tu1
ip add 192.168.255.200 255.255.255.0
tunnel source eth0/0
tunnel dest 192.1.20.70
tunnel mode gre ip
tunnel protection ipsec profile IPSEC
no shut
!
router eigrp 333
network 192.168.255.0 0.0.0.255
network 10.0.0.0
!
!
!-------
! R2
!-------
!
!create basic VTI tunnel with IPSec, pointing to R1
!
crypto isakmp policy 10
authentication pre-share
hash sha256
group 19
lifetime 3600
encryption aes 256
!
crypto isakmp key cisco123! address 192.1.23.23
!
crypto ipsec transform-set TFS esp-aes 256 esp-sha256-hmac
mode transport
!
crypto ipsec profile IPSEC
set transform-set TFS
!
int tu1
ip add 192.168.255.201 255.255.255.0
tunnel source eth0/0
tunnel dest 192.1.23.23
tunnel mode gre ip
tunnel protection ipsec profile IPSEC
no shut
!
router eigrp 333
network 192.168.255.0 0.0.0.255
network 10.0.0.0
!
!------
! ASA
!------
!
!create an ACL allowing UDP:500 (isakmp) and UDP:4500 (NAT-T) in on the outside interface; remember to use the post-NAT IP of R2, since NAT/UnNAT happens before ACL evaluation ;)
!
access-list OUTSIDE-IN extended permit udp host 192.1.23.23 host 192.168.70.7 eq isakmp
access-list OUTSIDE-IN extended permit udp host 192.1.23.23 host 192.168.70.7 eq 4500
!
access-group OUTSIDE-IN in interface OUTSIDE
!
!
!---------------------!
! Verifications !
!---------------------!
!
show crypto isakmp sa [detail]
chow crypto ipsec sa [detail]
debug crypto isakmp
!
!on ASA
!
show conn detail
show xlate detail
show nat detail
show asp drop
show access-listBefore allowing UDP:4500:
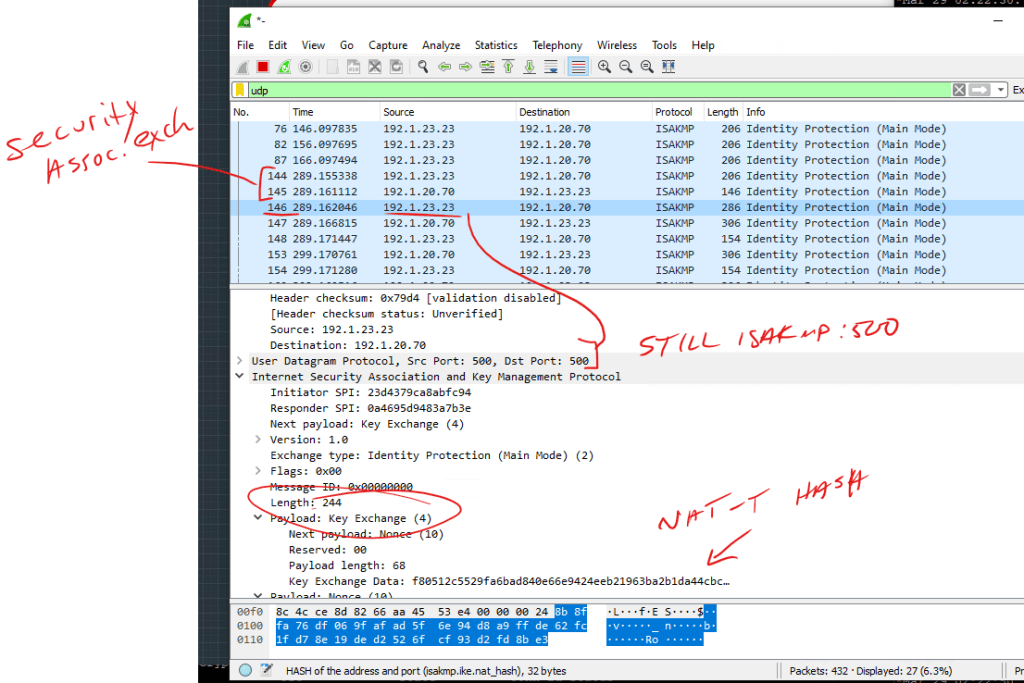
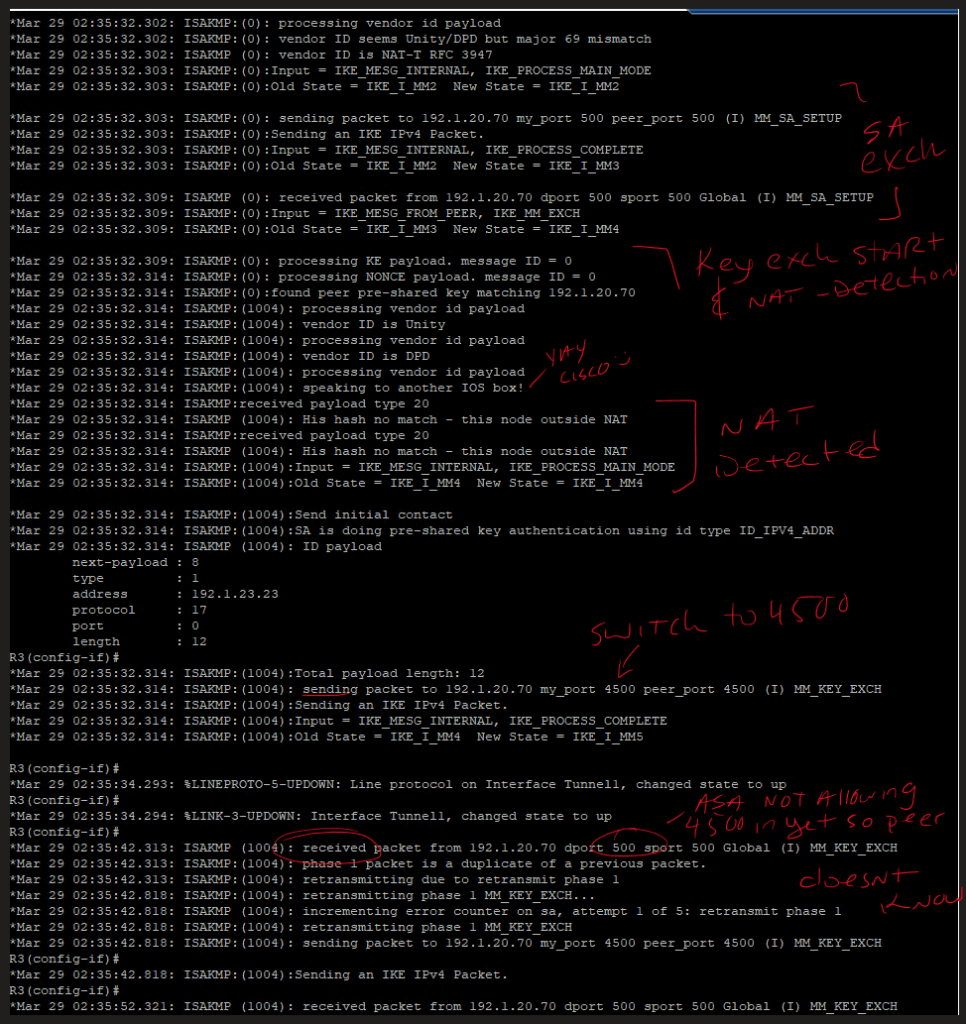
After allowing UDP:4500: