This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies. !—————————————–! ! fVRF IKEv1 and RSA-SIG Auth with sVTI ! !—————————————–! ! !RSA-Sig (certificate) based authentication can be done for ISAKMP peers in fVRF setup by using the isakmp-profile to specify the match…… Continue reading Study Notes – fVRF IKEv1 and RSA-SIG Auth with sVTI and default iVRF
Category: technical
Study Notes – Basic Front-Door VRF with Non-Default iVRF (ISAKMP PSK, GRE)
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies. !————————————————-! ! Basic Front-Door VRF with non-default LAN VRF ! !————————————————-! ! IKEv1 GREoIPSec L2L ! !————————————————-! ! !the purpose of Front Door VRF is to isolate the underlay and overlay networks, both…… Continue reading Study Notes – Basic Front-Door VRF with Non-Default iVRF (ISAKMP PSK, GRE)
Study Notes – Dual-Hub DMVPN Phase 1-3 w/ IPSec
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies. !—————–! ! DMVPN Phase I ! !—————–! ! Hub (R1) ! !—————–! ! ! cry isakmp policy 5 hash sha256 authen pre-share group 19 encry aes 256 ! cry isakmp key P@ssw0rd! address…… Continue reading Study Notes – Dual-Hub DMVPN Phase 1-3 w/ IPSec
Study Notes – Basic IOS CA Server Configuration and Use in IKEv1/ISAKMP VPN
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies. !————————————–! ! IOS CA Setup for IKEv1 VPN Auth ! !————————————–! ! CA Router (DMVPN Hub, usually) ! !————————————–! ! crypto key generate rsa modulus 2048 label Hub-CA-Keys ! ip http server !…… Continue reading Study Notes – Basic IOS CA Server Configuration and Use in IKEv1/ISAKMP VPN
Study Notes – Converting DMVPN Phase 1 to Phase 2 and 3
This is a post in a series of “stream-of-study” content where I post loosely-structured notes taken while labbing various scenarios and technologies. !——————–! ! Phase 2 DMVPN ! !——————–! ! HUB ! !——————–! !once Phase 1 is completely up and running, implement the following !change on the hub to allow spoke-to-spoke data plane forwarding !…… Continue reading Study Notes – Converting DMVPN Phase 1 to Phase 2 and 3
RFC and Standards Documents
In this post, I will keep a running tally of IETF RFC and/or IEEE Standards documents that are relevant to the CCIE Security v6 Lab exam and/or just useful references in general. This is in no particular order (for the time being) and should be considered a living document which I will update as things…… Continue reading RFC and Standards Documents
eBGP Multihop vs. eBGP TTL-Security
The following is a really great article by Jon Langemak examining the differences in router behavior when using eBGP multihop vs. eBGP ttl-security. http://www.dasblinkenlichten.com/ebgp-multihop-vs-ttl-security/ Check it out, it is well worth the read. By default, eBGP packets are sent with a TTL = 1, because we assume a directly-connected peer. If the peer is a…… Continue reading eBGP Multihop vs. eBGP TTL-Security
Cisco IOS Route-Based VPN with IKEv1 PSK GREoIPsec and EIGRP
This article will look at a basic configuration for a route-based VPN between two Cisco IOS routers, using IKEv1 and IPsec for tunnel protection, and EIGRP for dynamic route advertisements based on the above topology. Workflow: Verify basic routing and reachabilityCreate and configure: LAN networksTunnel interfaceEIGRP processVerify basic GRE tunnel status and reachabilityCreate and configure:…… Continue reading Cisco IOS Route-Based VPN with IKEv1 PSK GREoIPsec and EIGRP
Basic AnyConnect on Azure-hosted Meraki vMX
In this article, we’ll take a look at deploying a Meraki Virtual MX (vMX) in Microsoft Azure, and enabling a basic AnyConnect configuration on it for remote access VPN. This configuration includes a couple of specific steps required on the Azure side in order to properly allow inbound Anyconnect traffic to the vMX. Additional configurations…… Continue reading Basic AnyConnect on Azure-hosted Meraki vMX
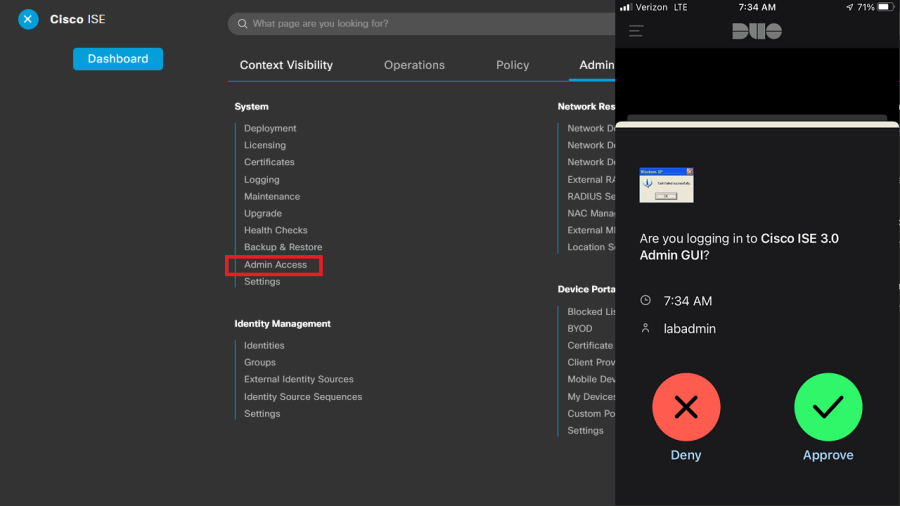
Duo MFA for the ISE Admin GUI
So, you’ve adopted ISE: 802.1x everywhere, maybe some CTS/SDA, posture for remote VPN endpoints, even dabbling with Threat-Centric NAC and some pxGrid integrations – life is good! The network feels secure, you’ve got lots of visibility and control. SASE and ZTA feel like attainable goals. Then, it hits you: you’ve put MFA in front of…… Continue reading Duo MFA for the ISE Admin GUI